ZEROBASE, The Infrastructure Layer Powering ZK Proofs

1. After Decentralization, What’s Left to Fix? The Role of ZK Proofs
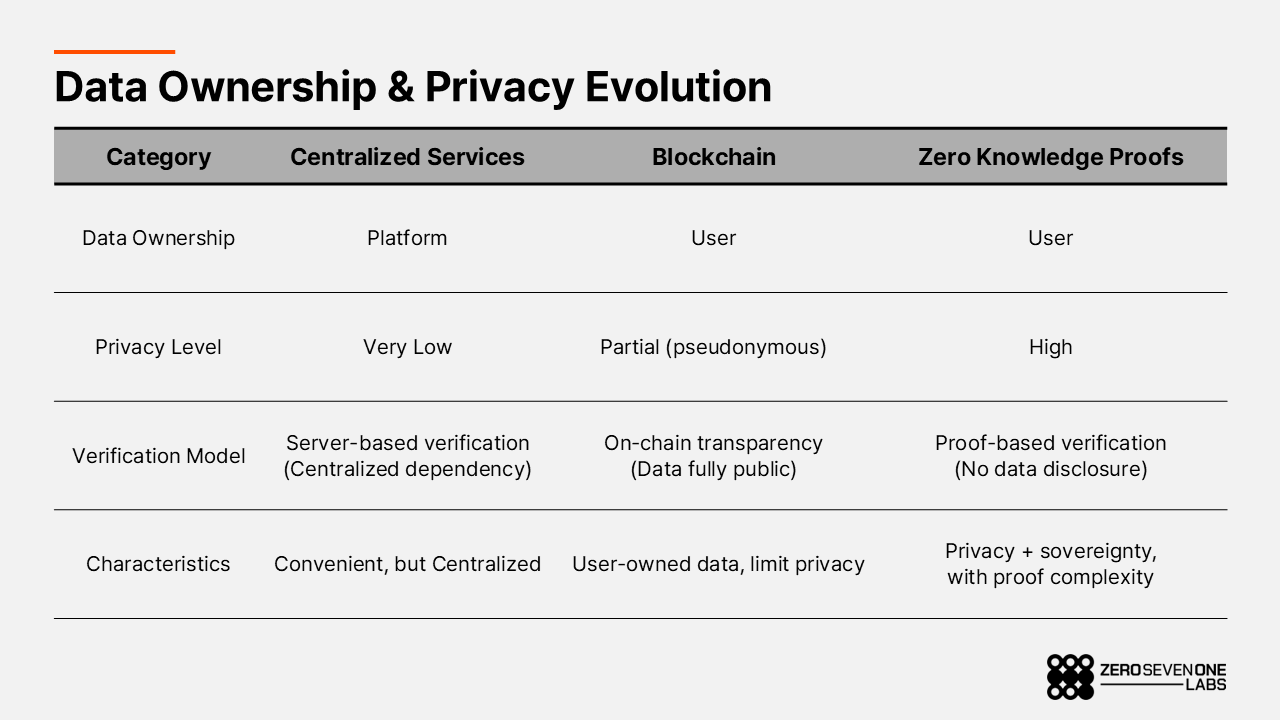
In the early days of the internet, freedom and openness of information were the core values. As we moved into the Web2 era, however, users stopped being just consumers and became constant producers of data. Search history, location data, payment records, social activity — all of this personal data effectively turned into platform-owned assets. Social networks and AI systems used that data to provide personalized experiences, but at the same time made it almost impossible for users to see or control what was being collected and how it was used. In practice, users were trading data sovereignty and privacy in exchange for convenience, and that structure became the default.
In this environment, a natural demand emerged: move the control of assets and transaction history away from centralized institutions and back to users. People started questioning whether it was really necessary for banks, payment processors, and platform servers to sit between users and their own transaction records. As one of the answers to that question, blockchains appeared.
What blockchains changed first and foremost was the ownership model of assets and transactions. In the traditional setup, banks, payment networks, and platforms maintained and verified users’ balances and transaction history in a centralized way. On a blockchain, users generate transactions themselves with their private keys and submit them to a decentralized network. Ownership and control over assets and transaction records shift from centralized entities to the user. And because data recorded on-chain cannot be arbitrarily modified or deleted, users gain a much stronger form of sovereignty over both assets and their histories.
Originally this structure was designed around money and financial assets, but in terms of ownership and control, it naturally extends to data sovereignty as well. As more types of state and data beyond token balances and transfers move on-chain, blockchains are evolving into not just asset ledgers but a data layer that users can directly control.
At the same time, blockchains are address-based systems and therefore do not provide full privacy. Every transaction is recorded on a public ledger; balances and transaction history are visible to anyone. If on-chain analysis is combined with KYC data or off-chain information, there is a real possibility that specific users can be deanonymized.
In other words, blockchains give individuals back control over their assets and transaction records, but they do not fully restore privacy sovereignty. The technology that can address this gap is ZK(Zero Knowkledge) proofs. A ZK proof is a cryptographic primitive that allows someone to prove that a statement about some data is true without revealing the data itself. With ZK, users can prove that their transactions or credentials are valid without exposing their underlying information.
Blockchains allow users to create and manage their own transactions, but the behavioral data generated in that process is still fully exposed. Addresses, balances, and transaction histories remain visible, which shows that “taking back control” and “protecting privacy” are related but distinct problems.
ZK proofs reduce this exposure. Users don’t need to reveal their wallet address or full transaction history. They can instead prove that they satisfy some condition. This makes it possible to preserve both asset and data sovereignty, while protecting privacy around how that data is used.
2. How ZK Proofs Work
At a high level, ZK systems work by generating a cryptographic proof from some hidden input, and having a third-party verifier check that proof to confirm whether the hidden input satisfies certain conditions.
The easiest way to understand a mathematically complex concept like ZK is to start by asking:
“How could I prove something is true without revealing the information itself?”
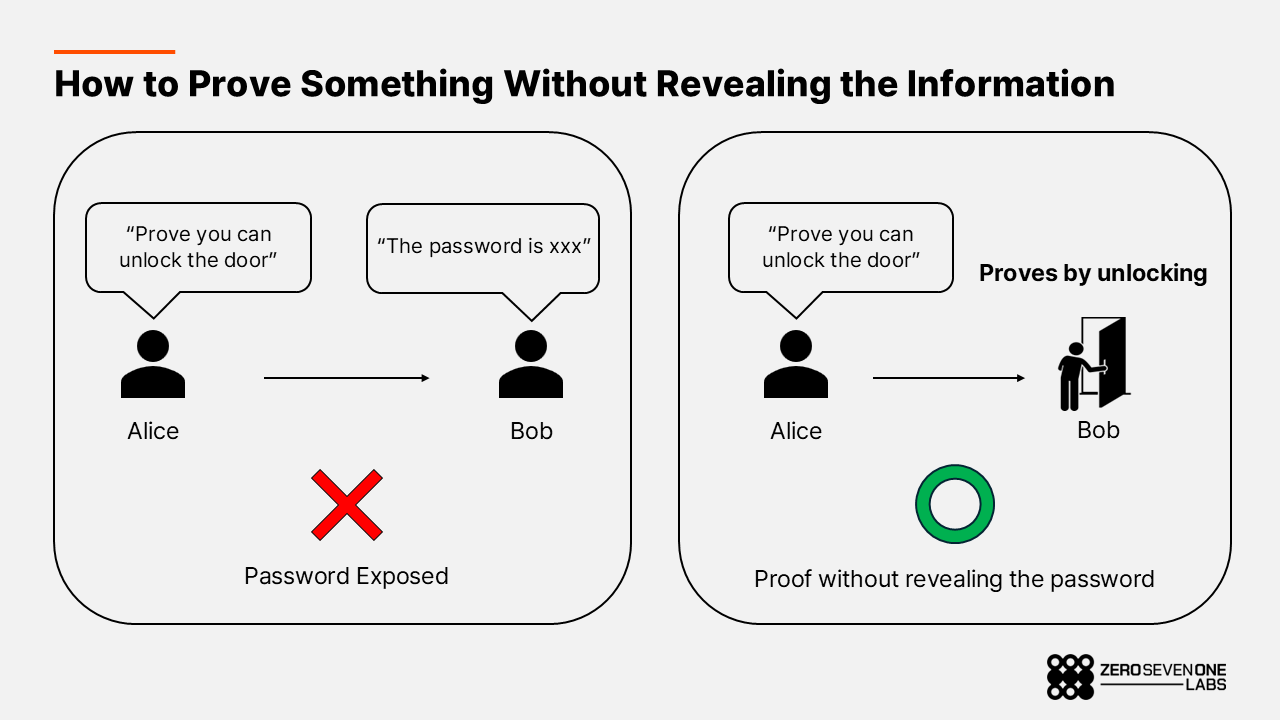
Imagine a company door lock that only opens when the correct passcode is entered. Bob knows the passcode, and he wants to prove to Alice that he really knows it.
He has two options.
First option – reveal the password.
Bob can simply say the code out loud or type it in front of Alice. This is the traditional authentication model. Alice can verify that Bob knows the code, but the secret itself is now fully exposed. Proof is achieved at the cost of zero privacy.
Second option – the ZK way.
Bob locks the door, then walks away. A moment later, he comes back and opens it in front of Alice without showing the keypad. Alice can confidently conclude that Bob knows the passcode, but she still has no idea what the code actually is. In this scenario, trust comes not from seeing the secret itself, but from observing the action of opening the door.
Real ZK systems follow this same pattern. The prover uses their secret input to generate a cryptographic proof that some statement is true. The verifier, using only the proof and a verification algorithm, can decide whether the claim is valid — without ever seeing the underlying data. The verifier learns nothing about the secret beyond the fact that the statement holds.
Blockchains and ZK Proofs
Blockchains are designed as fully transparent systems: every transaction and state transition is visible. Anyone can inspect balances and transaction histories, which makes it easy to verify the integrity of the system as a whole. But this full transparency is also what breaks individual privacy. If a specific address’s balance and transaction pattern are public, on-chain analysis can be used to infer user behavior or even identity.
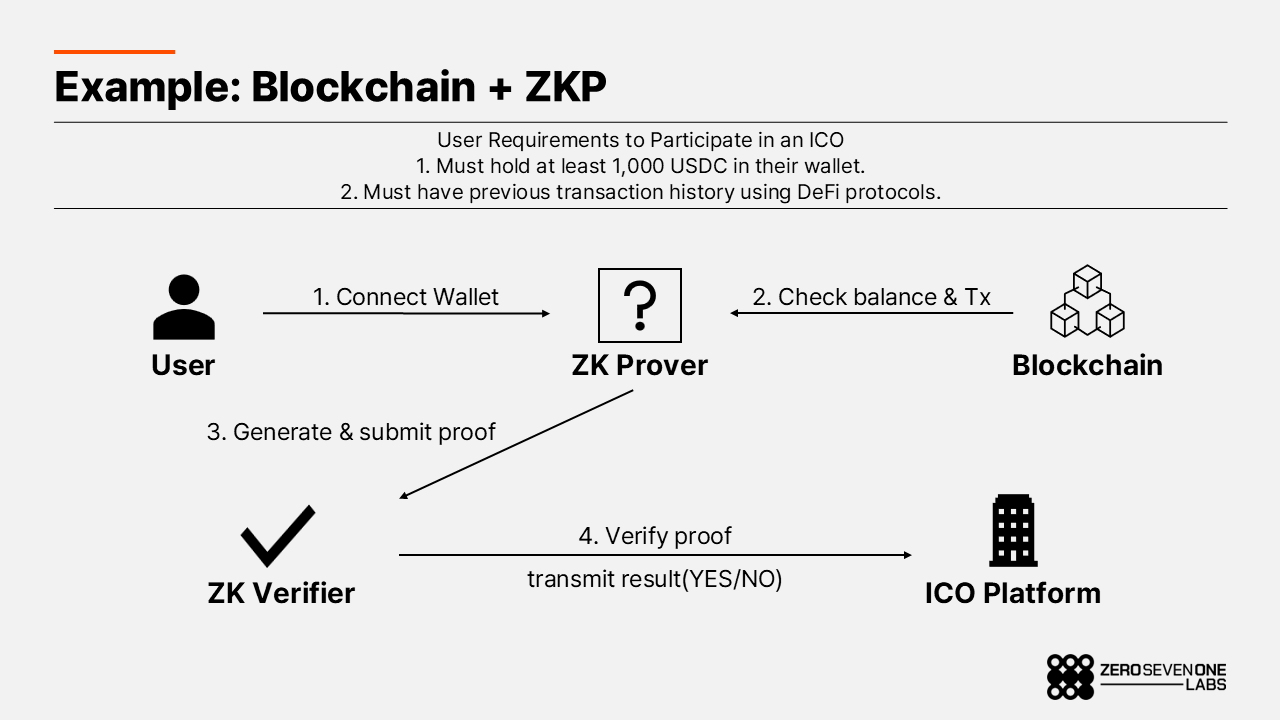
ZK proofs can address this privacy problem.
For example, suppose an ICO requires that participants:
Hold at least 1,000 USDC, and
Have prior transaction history using DeFi protocols.
In the traditional model, the user would have to reveal their wallet address and share their full balance and transaction history so the platform can check those conditions.
With ZK proofs, the user can instead generate a proof that both conditions are satisfied, without disclosing their address, their exact balance, or any specific transaction. The on-chain data remains private; only the fact that the conditions hold is exposed.
This idea generalizes far beyond asset proofs. ZK can be used to prove DAO token holdings for governance, to prove that someone has passed an exchange’s KYC process, or to prove both conditions at once — all without revealing raw data.
In short, ZK proofs add a new option to how blockchains handle data. Rather than always exposing raw information, we can selectively reveal only the truth of a statement. Traditional blockchains offer limited, address-level privacy; ZK enables a model where original data stays hidden while only the required outcome is proven.
3. ZEROBASE and ZK Proofs
3-1. Why ZK Proofs Were Hard to Use
ZK proofs have long been seen as a cryptographic tool that can deliver privacy and verifiability at the same time. But despite their promise, real-world usage of ZK in production systems has historically been very limited.
The main bottleneck is proof generation complexity. To use ZK, the original computation must be encoded as an arithmetic circuit, and the proof system must then prove that this circuit executed correctly. This transformation and proof generation step is orders of magnitude heavier than plain execution, which makes it hard to apply in latency-sensitive applications. On top of that, designing circuits requires deep cryptographic and low-level engineering expertise — far beyond what typical application developers are comfortable with.
There are also economic constraints. ZK proving requires high-performance compute, and someone has to operate and maintain that infrastructure. Without a clear incentive model, proving tends to remain in the hands of a few teams or organizations. Once proof generation becomes concentrated, the system inherits a new centralization vector that can undermine the very trust and privacy guarantees that ZK is meant to provide.
In practice, ZK proofs have been held back by high cost, slow performance, steep design complexity, and the risk of centralized operators. ZEROBASE was created to address exactly these pain points by turning proof generation into a distributed network that many participants can contribute to — rather than a closed, in-house infrastructure.
3-2. Making ZK Proofs Accessible
ZEROBASE restructures proof generation so that multiple nodes on a network can act as provers. The goal is to turn ZK proving into a shared resource that anyone can tap into, instead of something each project must build and operate on its own. This helps relax both cost and latency constraints and makes it more realistic to deploy ZK in live applications.
The network is organized into three logical roles:
Client – Any service or application that needs a ZK proof. Clients submit proof-generation requests for specific conditions they want to verify.
Hub – The coordination and validation layer. The Hub routes requests to prover nodes, monitors node status and heartbeats, verifies submitted proofs, and manages incentives and slashing.
Prover Node – A participant that actually generates proofs. Provers supply compute resources and are responsible for producing correct proofs within given time bounds.
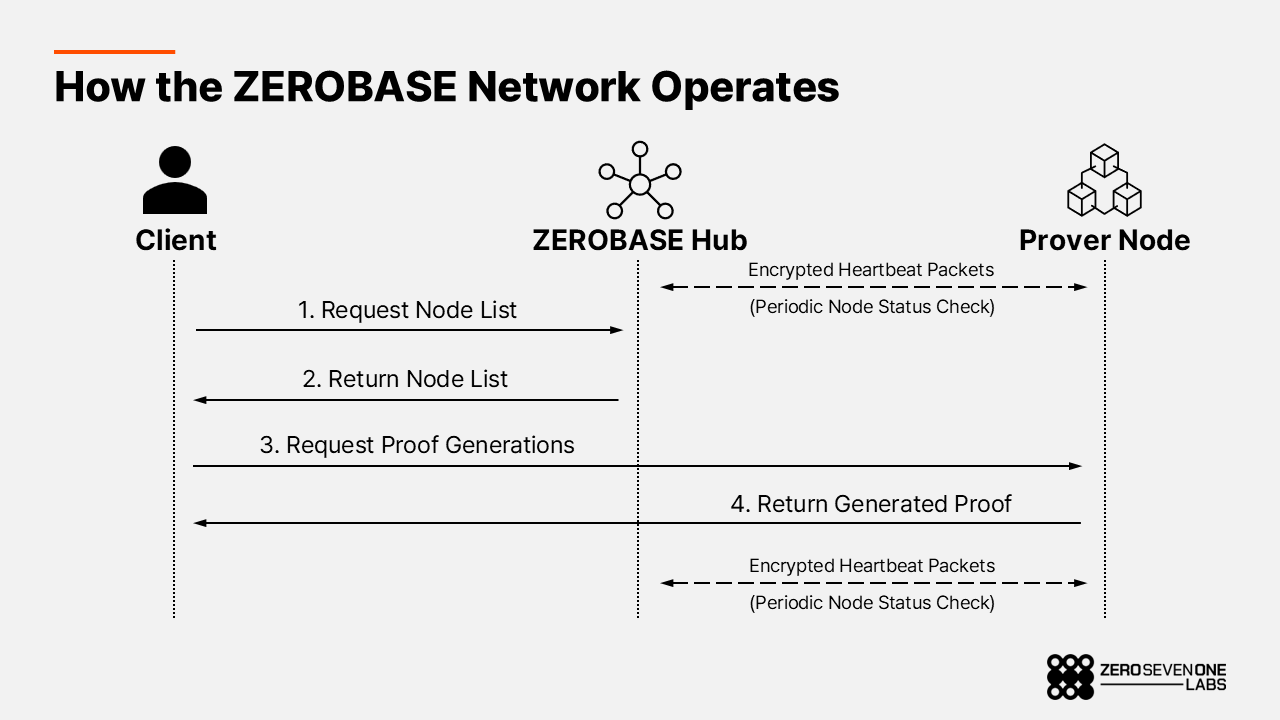
The Hub is the central coordinator of proof jobs. When a client submits a request, the Hub selects an available prover node and assigns the task. It continuously tracks node latency, health, and connectivity through encrypted heartbeat packets and reassigns work if a node becomes slow or unresponsive, so proof generation doesn’t stall. From the client’s perspective, there’s no need to manage node selection, monitoring, or scheduling — they simply call a single endpoint and receive a proof.
Prover nodes receive input data from clients, run the computation, and return a proof. Because proving is compute-intensive and time-sensitive, prover nodes typically run on GPU-backed infrastructure and are treated as accountable execution units responsible for both correctness and responsiveness.
This networked design allows proof generation to scale horizontally instead of relying on a single server. In practice, mid-complexity proofs — such as for login verification or transaction eligibility — can be generated in roughly 120 ms, which is fast enough for interactive user flows.
To maintain network reliability and economic alignment, ZEROBASE requires prover node operators to post at least $1M worth of stablecoins as collateral. If a node submits invalid proofs, behaves abnormally, or fails to respond within required time windows, part of this collateral can be slashed. Honest and performant nodes, on the other hand, earn rewards. This setup encourages only serious operators with robust infrastructure to join, and creates a competitive environment that keeps overall network quality high.
3-3. Trusting the Proof Generation Process Itself
ZEROBASE doesn’t stop at decentralizing proof generation. It also tackles the trust problem inside the proving process. In many traditional ZK deployments, proofs can be verified without revealing underlying data, but the machines that generate those proofs still see all of the raw inputs. That means prover operators can, in principle, read or leak sensitive information.
To address this, ZEROBASE integrates TEE (Trusted Execution Environment) technology. A TEE provides an isolated execution enclave inside the CPU, where data is processed in a way that is opaque even to the OS, the node operator, or the hardware vendor. With TEEs, ZEROBASE can ensure that the data used to generate a proof stays hidden throughout the entire proving workflow, even from the prover node itself.
In finance, enterprise, and public-sector systems, privacy protection and regulatory compliance often conflict. Personal data must be protected, but regulators and auditors still need a way to verify claims when necessary. Pure ZK constructions have historically lacked a practical, safe mechanism for selectively granting access in such scenarios.
TEE-based architecture gives ZEROBASE a foundation for selective disclosure models. By default, all sensitive inputs remain sealed inside the enclave and are only ever exposed in aggregated or proven form. Under tightly controlled conditions, however, the system can be configured so that authorized entities — for example, regulators or external auditors — can verify data or computations without the information being broadly exposed. This makes ZEROBASE’s model not just suitable for crypto-native environments, but also compatible with regulated finance and institutional use cases.
4. Applying ZK: ZK + X
As outlined earlier, the ZEROBASE network provides zero-knowledge proofs in a ZK-as-a-Service model. Developers no longer need to design complex circuits themselves or operate high-performance proving clusters; instead, they can use ZK proofs through simple network calls.
This shift turns proof generation from an infrastructure-building project into a straightforward API interaction. As a result, the cost of generating proofs decreases, proof speed becomes practical for real applications, and operational complexity drops significantly. These improvements allow zero-knowledge proofs to move beyond niche use cases and become a standard component of everyday services.
Consequently, ZK proofs are now becoming a natural choice not only for privacy-preserving features but also for any system that requires data integrity and verifiable actions.
4-1. ZEROBASE Staking
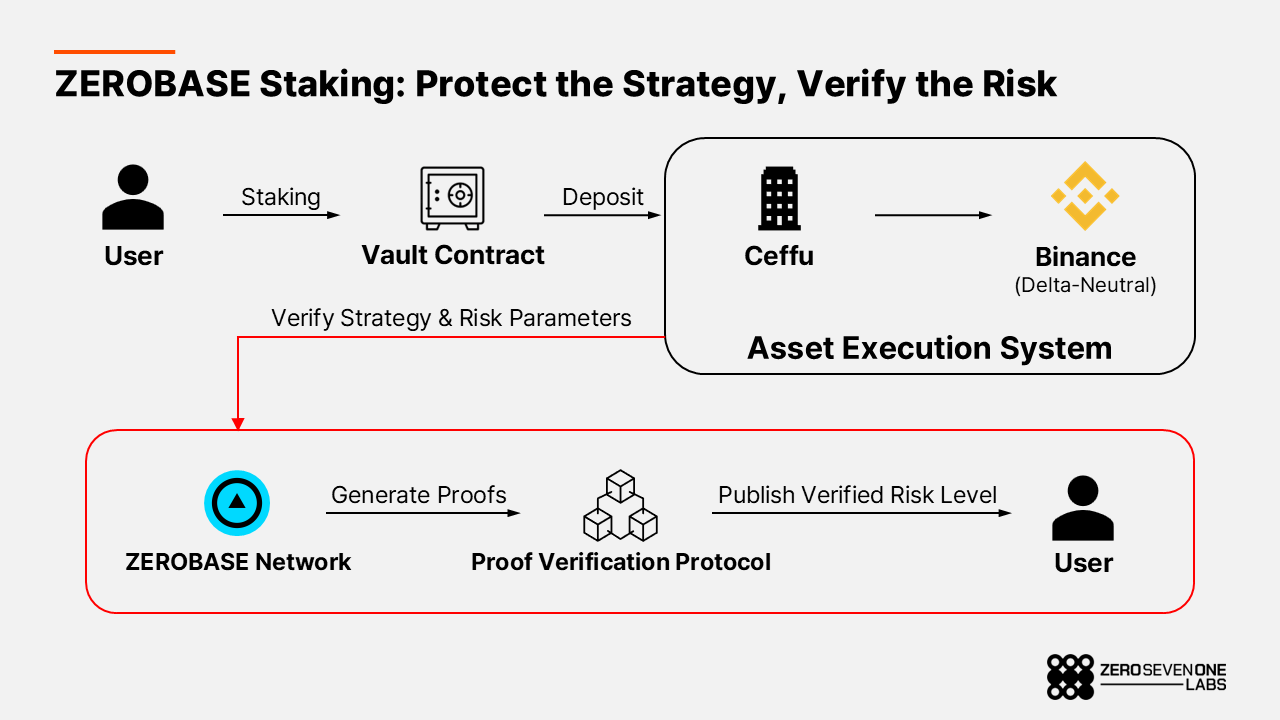
ZEROBASE Staking is a concrete example of how ZK proofs can be embedded directly into an asset management product.
When users stake stablecoins into the vault contract, funds are held securely via Ceffu (Binance Custody) and routed through MirrorX into Binance’s futures markets. There, capital is deployed into delta-neutral strategies that extract funding-rate yield while minimizing directional market exposure. In other words, the strategy is designed to behave in a market-neutral way.
Crucially, the details of the strategy remain private, while its risk profile and constraints are made transparently verifiable. Proof generation is handled by the ZEROBASE network, and the resulting proofs are verified by external protocols such as zkVerify and Aligned Layer. Proofs are produced every minute.
This architecture makes it possible to publicly verify that the strategy is operating within predefined risk bounds without revealing positions, execution logic, or proprietary edges. The strategy is protected from copycats or adversarial behavior, while its risk posture stays auditable.
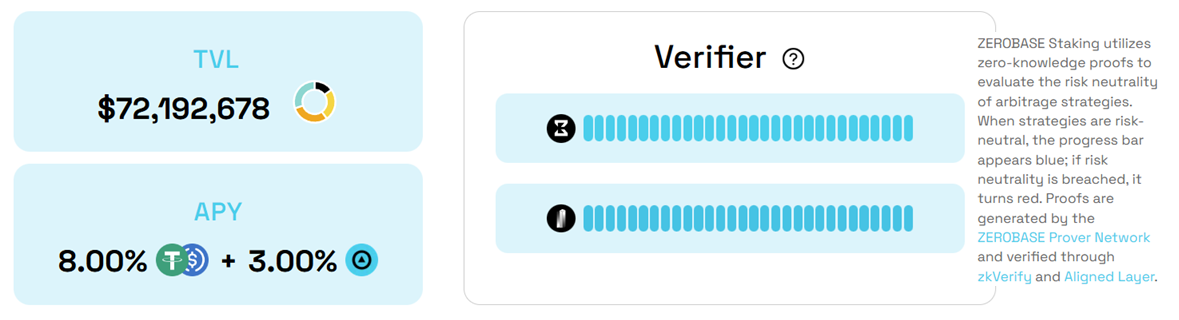
*When the strategy is delta-neutral, the on-site verification bar is shown in blue. If delta neutrality is breached, it turns red.
At the circuit level, the staking verification logic focuses on two core checks:
Delta-neutrality check – The circuit computes the difference between the maximum and minimum observed delta for the portfolio and proves that this spread lies within a predefined bound.
Leverage ratio check – The circuit verifies that leverage remains below a set limit and that the reported leverage matches the value computed from on-chain and off-chain inputs.
Because these proofs are produced on an ongoing basis, users can independently verify that the portfolio’s net delta exposure is kept in check, that leverage does not breach the permitted threshold, and that the strategy continues to operate within its predefined risk envelope. Rather than relying on the operator’s word, users rely on the ZK proofs themselves. ZEROBASE Staking is therefore a live example of a setup where the strategy details remain private, but risk is still provably constrained—something that is hard to replicate in traditional systems.
4-2. Real Usage of ZK Proofs
Zero-knowledge proofs are no longer a theoretical concept or a niche feature used only by a handful of projects. They are becoming a standard tool that can be applied directly within real services. ZEROBASE provides an environment where ZK proofs can be integrated naturally into service logic, enabling their use not only in privacy-sensitive areas but also in any system where transparency and trust are essential.
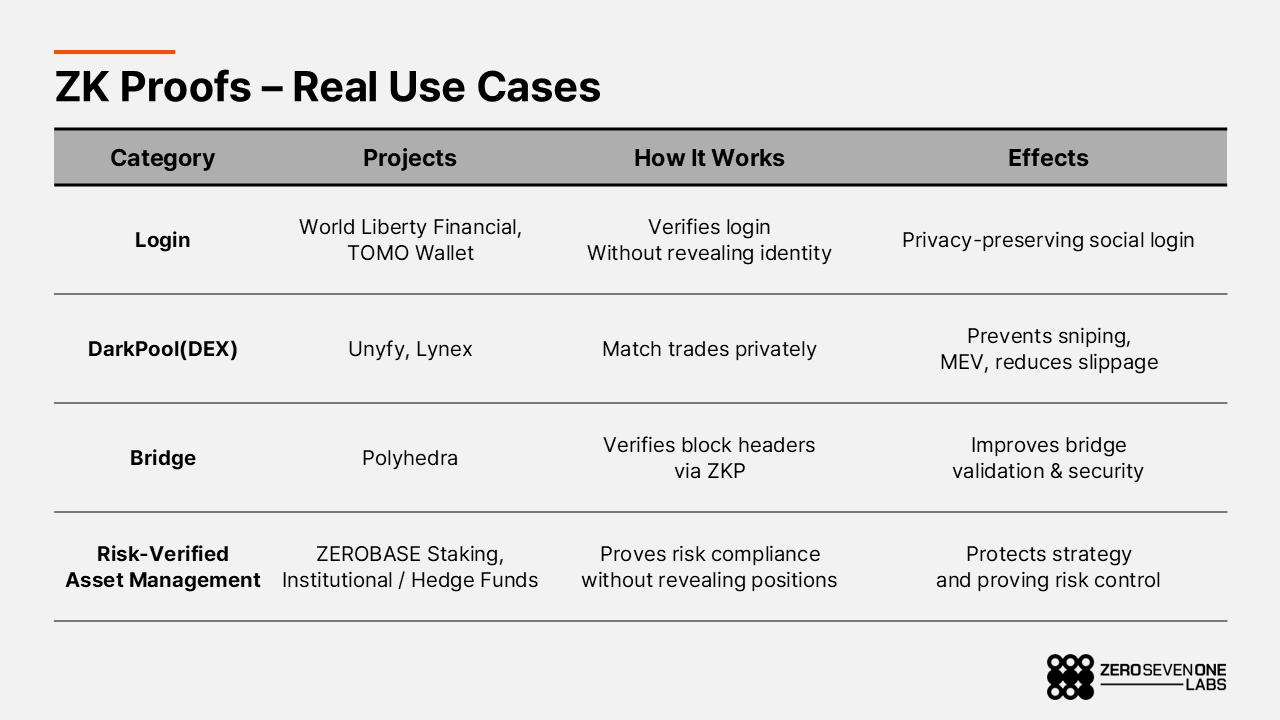
What matters here is that ZEROBASE is not pushing technology first and then forcing use cases on top of it. Instead, ZK proofs are being adopted at the points where they are genuinely needed. Examples include onboarding flows where users must prove they passed KYC, asset-management systems that must demonstrate adherence to risk limits, and environments where original data must remain hidden while regulators or auditors still require verifiable evidence. In both Web2 and Web3, existing services are beginning to use ZK proofs as a drop-in module wherever such requirements arise.
Because the proof system is applied only to the parts of a service where verification is actually needed, ecosystem growth follows real product demand rather than demo-driven or experimental deployments. This makes ZEROBASE’s ZK infrastructure practical and sustainable, as it can be plugged directly into systems that are already operating in production.
5. Conclusion
ZK proofs are not a mandatory ingredient for every service. At today’s level of performance and complexity, they are still far from being a default requirement. That’s why demand for proofs is not yet obvious at the surface. For a long time, ZK has been seen as “an important technology we’ll need someday,” rather than something essential right now.
But the environment is changing quickly. As AI becomes ubiquitous, platforms keep centralizing data collection, and privacy regulations tighten, demand is growing for ways to use data without exposing it. In that context, ZK is more than just a privacy-preserving tool; it is a new model for data usage — one where information does not need to be revealed to be trusted or useful.
ZEROBASE is aligned with this direction. Its goal is to turn ZK proofs into an infrastructure layer that any service can call, rather than a custom, in-house component. At the same time, it addresses a very practical issue: the risk that data used in proving might be exposed to node operators. By combining ZK with TEEs, ZEROBASE keeps sensitive data sealed during computation and enables architectures where only regulators or auditors, under strict conditions, can perform selective verification. The network can therefore support both strong privacy and regulatory compliance.
On top of this, ZEROBASE is rolling out Staking V3, zkCEX, and broader network expansion to push ZK into more production contexts. Over the long term, the vision is to embed ZK into banking and payment settlement flows, and to build financial infrastructure where asset management and risk control operate in a minimized-trust, verifiable way. In other words, the aim is for ZK to play a functional role inside real-world financial systems, not just crypto-native ones.
ZK proofs are only beginning to enter the phase of practical deployment. In an era defined by AI and data, where privacy and trust are becoming core values, the importance of ZK will only grow. It’s worth keeping an eye on how ZEROBASE evolves as a backbone infrastructure for this new ZK-powered world.
This research was prepared independently by the author(s). The project team may provide fact-checking input or feedback; however, to preserve data accuracy and objectivity, 071labs retains final editorial and publication control. The author(s) and/or 071labs may hold the cryptocurrencies/tokens referenced in this research and may have direct or indirect interests in the project (including, but not limited to, investments, advisory roles, or compensation). This research is provided for informational purposes only and does not constitute investment advice. Before making any investment decision, you should conduct your own research and, where appropriate, consult independent financial, tax, and legal advisors. Past performance does not guarantee future results.